Internal Penetration Testing
Internal Penetration Testing serves as a detailed internal security evaluation within your organization. This process entails a meticulous examination of your internal IT framework, encompassing servers, workstations, network devices, and applications. The objective is to methodically uncover and assess vulnerabilities that could potentially be exploited by insiders. This form of testing methodically replicates various internal risk scenarios, including potential employee misconduct or procedural errors. The primary aim is to ensure the robust protection of your organization’s sensitive data and critical internal processes. By systematically identifying and remedying these vulnerabilities, we enhance your internal defense mechanisms, significantly bolstering your organization’s resilience to internal security threats.

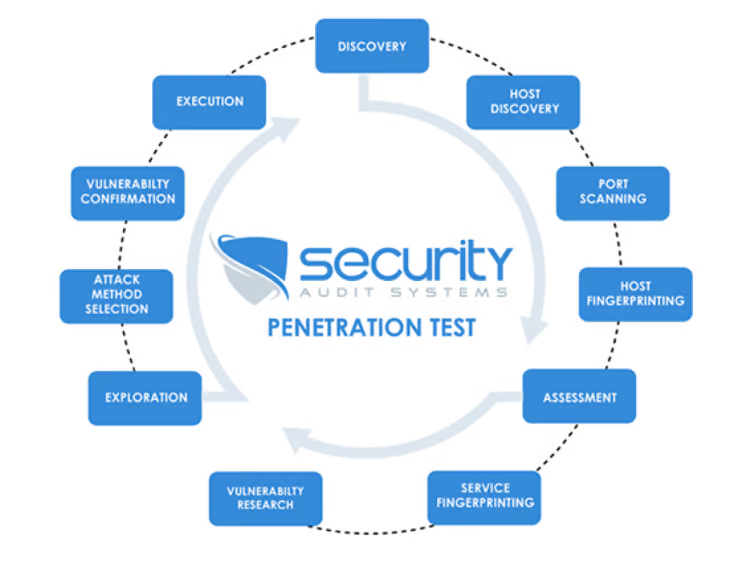
Our Methodology
Our approach to Internal Penetration Testing is comprehensive and methodical, subtly incorporating the principles of the PTES and NIST frameworks, ensuring a thorough and effective assessment:
- Initial Analysis and Planning: We begin by understanding your internal network environment, mapping out critical assets, and establishing the scope of the assessment.
- Threat Identification: Our team identifies potential internal threats and vulnerabilities, considering various insider threat scenarios.
- Vulnerability Assessment: We conduct a thorough examination of your internal systems, identifying vulnerabilities that could be exploited from within.
- Control Analysis: We evaluate the effectiveness of existing security controls and procedures in place within your organization.
- Exploitation: Simulating controlled internal attacks, we assess the impact of successful exploits on your network.
- Post-Exploitation Analysis: After exploitation, we evaluate the depth of access and potential damage, assessing the data at risk.
- Reporting and Recommendations: A comprehensive report is provided, detailing our findings with actionable recommendations for enhancing your internal security posture.
Why Choose Us for Your Internal Pentesting Needs?
- Customized Security Strategies: We recognize the uniqueness of every organization. Our services are tailored to align with your specific internal security needs and business objectives.
- Commitment to Confidentiality: We handle all information with the highest level of confidentiality, ensuring the integrity and privacy of your internal data during and after the testing process.
- Comprehensive and Understandable Reporting: Our reports are detailed yet accessible, providing clear insights and practical recommendations to strengthen your internal security.
- Continuous Support and Guidance: We don’t just identify vulnerabilities; we partner with you in developing a robust security culture within your organization. Our support extends beyond the initial assessment, providing guidance for ongoing security enhancement.

