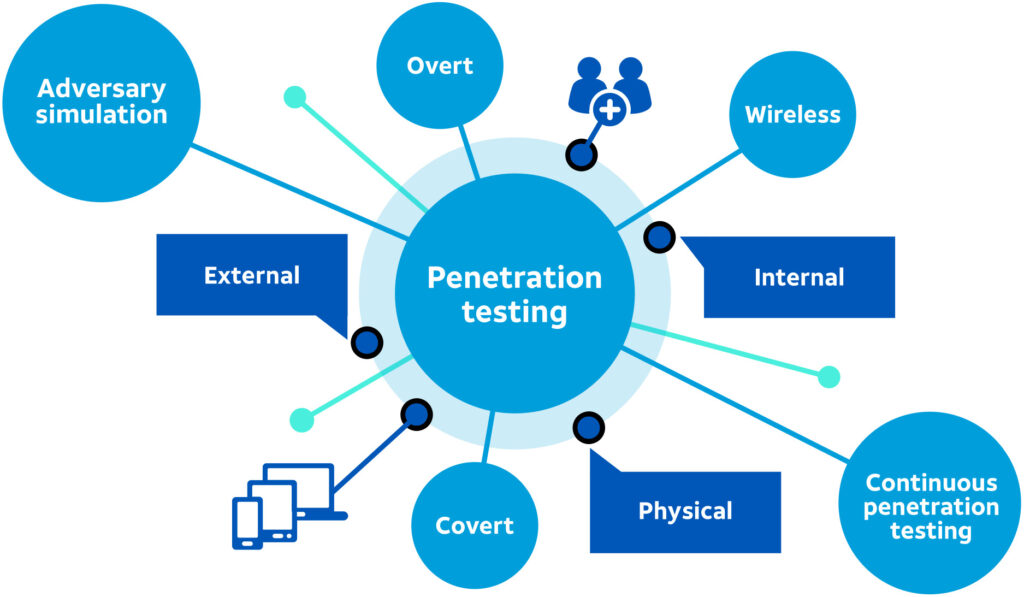
How We Conduct Web Application Penetration Testing: An OWASP-Based Approach

Our approach to web application penetration testing is rooted in the guidelines provided by the Open Web Application Security Project (OWASP), an international non-profit organization dedicated to improving software security.
- Planning and Reconnaissance: Initially, we define the scope of the test and gather as much information as possible about the target application. This includes understanding the technology stack, functionalities, and user roles.
- Scanning and Analysis: Utilizing a combination of automated tools and manual techniques, we scan the web application to identify vulnerabilities such as SQL injection, Cross-Site Scripting (XSS), and security misconfigurations.
- Exploitation: In this phase, we attempt to exploit identified vulnerabilities in a controlled and safe manner. This helps us understand the impact of each vulnerability and the potential damage it could cause.
- Reporting and Recommendations: After the testing, we provide a comprehensive report detailing our findings. This report includes a description of the vulnerabilities, their severity, and practical recommendations for remediation.
- Post-Test Review and Compliance: We also offer post-test reviews to ensure that all vulnerabilities have been adequately addressed. Additionally, we ensure that your web application complies with relevant regulations and industry standards.
- Continuous Monitoring and Improvement: Security is an ongoing process. We emphasize the importance of continuous monitoring and periodic retesting to adapt to new threats and maintain a robust security posture.
Exterior Structuring
Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industryu2019s standard dummy text ever since the 1500s, scrambled it to make a type specimen book.
It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the.
Why Choose Our OWASP-Aligned Web Application Penetration Testing Services?
Our services are designed to provide a thorough and effective assessment of your web application’s security. By aligning our testing methodology with OWASP standards, we ensure that your applications are tested against the most relevant and up-to-date security risks. Our team of experienced cybersecurity professionals is committed to delivering actionable insights and pragmatic solutions to protect your web assets.

Conclusion
In today’s interconnected world, the security of web applications is not just a technical necessity but a business imperative. By opting for our OWASP-aligned web application penetration testing services, you are taking a significant step towards safeguarding your digital assets and maintaining the trust of your stakeholders.
